Project Objective
The primary objective of this project is to implement AES Cryptographic algorithm by achieving higher throughput which will make the cryptographic system to be comparatively faster than ever. Moreover, it is also intended to achieve lower area so that we can have a compact design of AES Cryptography. It is the known fact that hardware implementation of a system provides better results than the software implementation. That’s the reason that this project is implemented on FPGA (Field programmable gate arrays).
Socio-Economic Benefits
With the rapid development in field of information technology, the need to have secured communication has increased vastly. Plus, the demand for faster system with minimum possible size is significant in the market. It is the need of the time not only at military, political and diplomatic level but is also required for common man as well.
As we bank, shop, and communicate online, digital security is becoming increasingly critical to protect our data. Encryption is the foundation of that security. Cyber hackers are continuously attempting to steal our personal information.
Following are the real life applications of this project
- Authentication/Digital Signatures
- Online money transactions
- Secure Network Communications
- Healthcare (Research Data of Hospitals)
- ATM Machine
- Secured confidential communication
Project Methodology
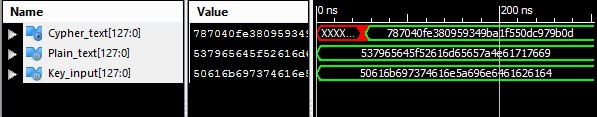
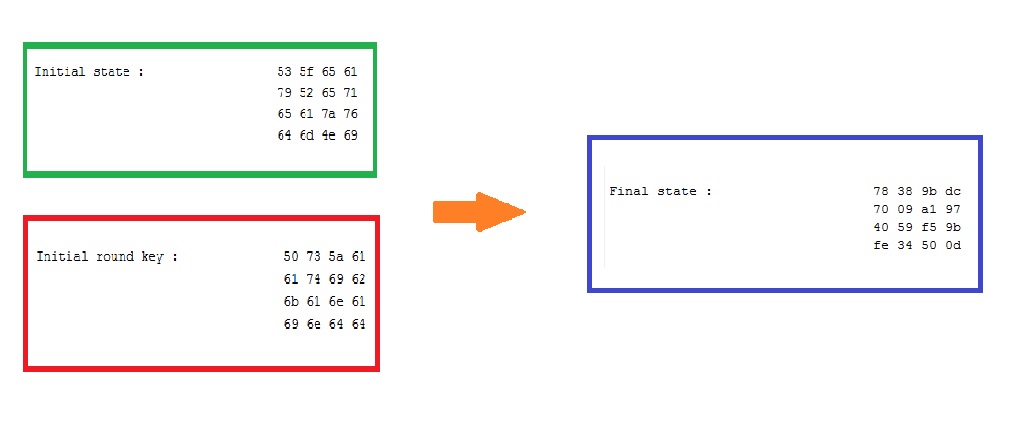
AES is one of the symmetric cryptographic algorithm which involve the sharing of secret/private key for successful Encryption and Decryption. The varying key length and changing number of rounds with respect to key lengths make it more secure and more efficient than DES. For 128 bit Encryption, there are total 10 rounds and in each round, there are 4 basic operations: Byte Substitution, Shift Rows, Mix Column and Add Round Key. Most of Throughput of Encryption part of AES algorithm depends on Byte Substitution and Mix Column. So different architectures of S-box and Mix Column have been retrieved from literature and are compared to get the most faster and compact design of AES.
There are many different approaches for implementing Substitution Box (S-Box), one is using look Up Table approach which is very simpler to implement but in this case we have to bear with unavoidable delay of LUTs. Second approach is to implement it with the help of 2*4 Decoders and 4*1 Multiplexers. In this approach the whole S-Box is divided into 4 groups and on the basis of most significant two bits of input byte(Byte to be substituted from S-box), which acts as input to 2*4 decoder only 1 out of 4 groups will be enabled. This group consist of 4 rows and 4 columns total consisting of sixteen 2*2 LUTs containing 64 bytes. Using next 4 bits of input byte, one of LUT will be selected and then finally on the basis of two least significant bits which acts as select lines to 4*1 MUX, only one byte out of 4 will appear at output which will be the desired byte. The other approach avoids use of LUTs and proposes use of composite field data path for creation of S-Box. All of these approaches have been implemented and compared.
Other most crucial operations of AES are Mix Column (for Encryption) and Inverse Mix Column (For Decryption) and in these operations, there are predetermined constant Matrix. Multiplication in Galois Filed is very tricky and time consuming. So instead of direct multiplication, making separate 16*16 LUTs containing all possible results after multiplication with constants can be one approach. Other approach that we can adopt is normal multiplication but the problem is that the result of multiplication will not belong to GF (2^8). This result can be reduced to 8 bits very efficiently by xor-ing it with predetermined constant.
This project achieves the faster and compact design of AES by comparing these different architectures and finding the best in term of Throughput/Area ratio.
Project Outcome
We have successfully implemented the most possible advanced and compact design for AES Cryptographic system. The goals addressed in our objectives are achieved. The throughput achieved is approximately 700MHz and the speed area ratio is 12.4 which proves it to be a fastest and a compact design which can be applicable for ATM machines, online communications etc.